Major firms hit as Petya virus sweeps from Ukraine to US
28 Jun 2017
Computer systems from Ukraine to the United States were struck on Tuesday in an international cyberattack that was similar to a recent assault that crippled tens of thousands of machines worldwide.
 The hackers have caused widespread disruption across Europe, hitting Ukraine especially hard.
The hackers have caused widespread disruption across Europe, hitting Ukraine especially hard.
Company and government officials reported serious intrusions at the Ukrainian power grid, banks and government offices. Russia's Rosneft oil company also reported falling victim to hacking, as did Danish shipping giant A P Moller-Maersk and French construction materials company Saint Gobain. British advertising giant WPP said it too was among the victims of the cyberattack.
In Kiev, the capital of Ukraine, ATMs stopped working. About 80 miles away, workers were forced to manually monitor radiation at the old Chernobyl nuclear plant when their computers failed. And tech managers at companies around the world - from Maersk, the Danish shipping conglomerate, to Merck, the drug giant in the United States - were scrambling to respond. Even an Australian factory for the chocolate giant Cadbury was affected.
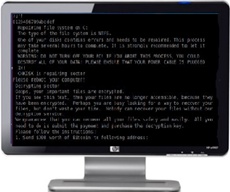
Ukrainian deputy prime minister Pavlo Rozenko on Tuesday posted a picture of a darkened computer screen to Twitter, saying that the computer system at the government's headquarters has been shut down. Prime Minister Volodymyr Groysman said the attack was ''unprecedented'' but ''vital systems haven't been affected''.
It was unclear who was behind this cyberattack, which started as an attack on Ukrainian government and business computer systems - an assault that appeared to have been intended to hit the day before a holiday marking the adoption in 1996 of Ukraine's first Constitution after its break from the Soviet Union. The attack spread from there, causing collateral damage around the world.
The outbreak was the latest and perhaps the most sophisticated in a series of attacks making use of dozens of hacking tools that were stolen from the National Security Agency and leaked online in April by a group called the Shadow Brokers (See: Hacking group publishes NSA exploits online).
Like the WannaCry attacks in May, the latest global hacking took control of computers and demanded digital ransom from their owners to regain access. The new attack used the same National Security Agency hacking tool, Eternal Blue, that was used in the WannaCry episode, as well as two other methods to promote its spread, according to researchers at the computer security company Symantec (See: Major cyber-attack hits nearly 100 countries; Asia mostly spared).
The National Security Agency has not acknowledged its tools were used in WannaCry or other attacks. But computer security specialists are demanding that the agency help the rest of the world defend against the weapons it created.
The vulnerability in Windows software used by Eternal Blue was patched by Microsoft in March, but as the WannaCry attacks demonstrated, hundreds of thousands of groups around the world failed to properly install the fix.
Because the ransomware used at least two other ways to spread on Tuesday - including stealing victims' credentials - even those who used the Microsoft patch could be vulnerable and potential targets for later attacks, researchers at F-Secure, a Finnish cybersecurity firm, and others told The New York Times.
A Microsoft spokesman said the company's latest antivirus software should protect against the attack.
Ukrainian officials pointed a finger at Russia on Tuesday, although Russian companies were also affected. Home Credit bank, one of Russia's top 50 lenders, was paralysed, with all of its offices closed, according to the RBC news website. The attack also affected Evraz, a steel manufacturing and mining company that employs about 80,000 people, the RBC website reported.
In the United States, the multinational law firm DLA Piper also reported being hit. Hospitals in Pennsylvania were being forced to cancel operations after the attack hit computers at Heritage Valley Health Systems, a Pennsylvania health care provider, and its hospitals in Beaver and Sewickley, Penn., and satellite locations across the state.
The ransomware also hurt Australian branches of international companies. DLA Piper's Australian offices warned clients that they were dealing with a ''serious global cyber incident'' and had disabled email as a precautionary measure. Local news reports said that in Hobart, Tasmania, on Tuesday evening, computers in a Cadbury chocolate factory, owned by Mondelez International, had displayed ransomware messages that demanded $300 in bitcoins.
Qantas Airways' booking system failed for a time on Tuesday, but the company said the breakdown was due to an unrelated hardware issue.
The Australian government has urged companies to install security updates and isolate any infected computers from their networks.
''This ransomware attack is a wake-up call to all Australian businesses to regularly back up their data and install the latest security patches,'' said Dan Tehan, the cybersecurity minister. ''We are aware of the situation and monitoring it closely.''
A National Security Agency spokesman referred questions about the attack to the Department of Homeland Security. ''The Department of Homeland Security is monitoring reports of cyberattacks affecting multiple global entities and is coordinating with our international and domestic cyber partners,'' Scott McConnell, a department spokesman, said in a statement.
Computer specialists said the ransomware was very similar to a virus that emerged last year called Petya. Petya means ''Little Peter,'' in Russian, leading some to speculate the name referred to Sergei Prokofiev's 1936 symphony ''Peter and the Wolf,'' about a boy who captures a wolf.
Reports that the computer virus was a variant of Petya suggest the attackers will be hard to trace. Petya was for sale on the so-called dark web, where its creators made the ransomware available as ''ransomware as a service'' - a play on Silicon Valley terminology for delivering software over the internet, according to the security firm Avast Threat Labs.
That means anyone could launch the ransomware with the click of a button, encrypt someone's systems and demand a ransom to unlock it. If the victim pays, the authors of the Petya ransomware, who call themselves Janus Cybercrime Solutions, get a cut of the payment.
That distribution method means that pinning down the people responsible for Tuesday's attack could be difficult.



















