Computer crime in India
By Shehla Raza Hasan | 28 Mar 2003
 Kolkata:
We often receive e-mails warning us that
a new virus is doing the rounds and advising us about how to protect
ourselves from it. Software firms work round the clock
to develop antidotes for these viruses. We also read stray
reports of persons being caught for hacking websites and
similar indiscretions. With the onset of the digital age,
there is a growing realisation that we live in an age
in which cyber crime is a reality.
Kolkata:
We often receive e-mails warning us that
a new virus is doing the rounds and advising us about how to protect
ourselves from it. Software firms work round the clock
to develop antidotes for these viruses. We also read stray
reports of persons being caught for hacking websites and
similar indiscretions. With the onset of the digital age,
there is a growing realisation that we live in an age
in which cyber crime is a reality.
The Computer Crime & Abuse Report (India) 2001-02 has come out with startling data related to these crimes. The report analyses 6,266 incidents of computer crime and abuse that affected 600 organisations spanning IT, manufacturing financial services, education, telecommunications, healthcare and other services sectors in India during this period. The report has been published by the Computer Emergency Response Team of the Asian School of Cyber Laws.
This data is only the tip of the proverbial iceberg. Like most crimes, these largely go unreported, mainly because people are not aware of laws governing cyber crimes. Says a deputy commissioner of police in Kolkata: “Most people are not aware that there are laws governing cyber crime. Therefore a good many of them go unreported. If reported, these cases are taken very seriously.”
The reasons for not reporting are also varied. The report says that 23 per cent of the organisations did not know that the police were equipped to handle cyber crime, 8 per cent had no awareness of the cyber law, and 9 per cent feared further attacks, while a good 60 per cent wanted to avoid negative publicity.
The passage of the Information Technology Act 2000 and subsequent amendments to the Indian Penal Code and the Evidence Act have paved the way for stringent penalties for computer crimes. The law envisages imprisonment up to 10 years and damages in crores of rupees for various computer crimes. Cyber crime investigation cells have been set up in various cities. Bangalore has a dedicated cyber crime police station.
In the light of ever-increasing white-collar crimes, it would be worthwhile to look at an interesting set of facts and figures related to cyber crime.
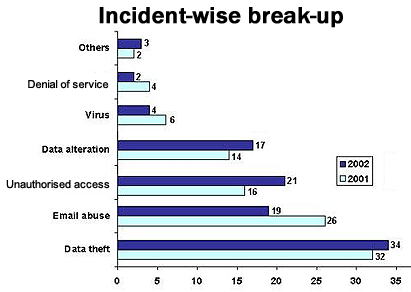
The above figures give the percentage break-up of incidents and categories of crime. Almost 60 per cent of the incidents in the year were reported in the first six months of the year and the maximum number of incidents were reported in September and the minimum in August. Another interesting fact is that almost 60 per cent were reported on Mondays, Fridays and Saturdays and a minimum number on Sundays.
The perpetrator-wise break-up shows that the largest number of incidents was attributable to former employees (31 per cent) and the second slot was by business rivals (29 per cent). What is interesting is that more than half the incidents are attributable to employees (current as well as former).
 Those
attacks where sophisticated techniques and methodologies
were used have been classified as ‘hacker’,
constituting 11 per cent, while those done by persons
with relatively low knowledge are classified as ‘script
kiddies’; these constitute 8 per cent of the
perpetrators of crime. What is disturbing is that the
script kiddies have successfully penetrated organisational
networks using freely available hacking tools.
Those
attacks where sophisticated techniques and methodologies
were used have been classified as ‘hacker’,
constituting 11 per cent, while those done by persons
with relatively low knowledge are classified as ‘script
kiddies’; these constitute 8 per cent of the
perpetrators of crime. What is disturbing is that the
script kiddies have successfully penetrated organisational
networks using freely available hacking tools.
Various categories of crime have been enumerated along with data related to them.
Data
theft
This category accounted for 33 per cent of the total
reported incidents. These included theft and misappropriation
of electronic information and records. Incidents of
unauthorised access where no data was stolen have not
been included. In the category of data theft, stealing
of source code topped the list with 37 per cent, followed
by those of credit card details (29 per cent). Theft
of details of business plans accounted for 20 per cent
and the rest was 14 per cent.
E-mail
abuse
This refers to three categories of abuse — obscene
e-mails (60 per cent), threatening ones (25 per cent)
and defamatory matter (15 per cent).
Data
alteration (on the rise)
One of the potentially most dangerous kinds of cyber
crimes constituted 14 per cent of the incidents reported
in 2001. It rose to 17 per cent of the incidents reported
in 2002. This category relates to incidents where unauthorised
alteration of vital information has taken place and
data has been doctored or tampered with, in order to
misrepresent facts.
Such crimes include alteration of hospital records, unauthorised changes made to quotations, financial accounts and bank records. Interestingly, there were many instances where persons having authorised access to the data made the unauthorised alteration.
Unauthorised
access
This category accounted for 19 per cent of the total
incidents. Methods employed for unauthorised access
included malicious code (38 per cent), social engineering
(29 per cent), remote dial-in (18 per cent) and Internet-based
methods (15 per cent).
Virus
This category referred only to those incidents where
viruses were sent deliberately to particular victims.
This category reflected 14 per cent of the total incidents,
but is significant because of the damage potential.
Denial
of service
These included denial of service attacks on web and
mail servers, FTP servers and printers. This category
accounted for 3 per cent of the incidents reported.
In 95 per cent of the cases these attacks appeared to
originate from outside India.
 According
to an abstract prepared by the Asian School of Cyber
Laws, incidents of data theft, data alteration and
unauthorised access can be eliminated by the proper
use of public key infrastructure (PKI). PKI is the super
system that puts in place policies, people, processes
and technology to harness the power of cryptography
and its applications like digital signatures.
According
to an abstract prepared by the Asian School of Cyber
Laws, incidents of data theft, data alteration and
unauthorised access can be eliminated by the proper
use of public key infrastructure (PKI). PKI is the super
system that puts in place policies, people, processes
and technology to harness the power of cryptography
and its applications like digital signatures.
The Indian law specifically recognises digital signatures as being the only accepted mode of authentication of electronics records. While India is one of the first countries to have granted legal recognition to PKI, its use remains minimal primarily because of a lack of awareness about its benefits.
A PKI-based system would help in achieving the objectives of information security, namely privacy, data integrity, entity authentication and identification, message authentication, signature authorisation, validation and access control, certification, time stamping, witnessing, receipt confirmation, ownership, anonymity, non-repudiation and revocation.
It
is clear that there is a crying need to spread awareness
about cyber laws and how to tackle cyber crimes. It
is time we put up a tough battle for cyber criminals.
Latest articles
Featured articles

Server CPU Shortages Grip China as AI Boom Strains Intel and AMD Supply Chains
By Cygnus | 06 Feb 2026
Intel and AMD server CPU shortages are hitting China as AI data center demand surges, pushing lead times to six months and driving prices higher.

Budget 2026-27 Seeks Fiscal Balance Amid Rupee Volatility and Industrial Stagnation
By Cygnus | 02 Feb 2026
India's Budget 2026-27 targets fiscal discipline with record capex as markets tumble, the rupee weakens and manufacturing struggles to regain momentum.

The Thirsty Cloud: Why 2026 Is the Year AI Bottlenecks Shift From Chips to Water
By Axel Miller | 28 Jan 2026
As AI server density surges in 2026, data centers face a new bottleneck deeper than chips — the massive water demand required for cooling next-generation infrastructure.

The New Airspace Economy: How Geopolitics Is Rewriting Aviation Costs in 2026
By Axel Miller | 22 Jan 2026
Airspace bans, sanctions and corridor risk are forcing airlines into costly detours in 2026, raising fuel burn, reducing aircraft utilisation and pushing airfares higher worldwide.

India’s Data Center Arms Race: The Battle for Power, Cooling, and AI Real Estate
By Cygnus | 22 Jan 2026
India’s data centre boom is turning into an AI arms race where power contracts, liquid cooling and fast commissioning decide the winners across Mumbai, Chennai and Hyderabad.

India’s Oil Balancing Act: Refiners Rebuild Middle East Supply Lines as Russia Flows Disrupt
By Axel Miller | 21 Jan 2026
India’s refiners are rebalancing crude sourcing as Russian imports fell to a two-year low in December 2025, lifting OPEC’s share and raising geopolitical risk concerns.

Arctic Fever: How ‘Greenland Tariff’ Politics Sparked a Global Flight to Safety
By Axel Miller | 20 Jan 2026
Greenland-linked tariff threats have injected fresh uncertainty into transatlantic trade, triggering a risk-off shift in markets and reshaping global supply chain planning.

The New Oil (Part 5): Friend-Shoring, Supply Chain Fragmentation and the Cost of Resilience
By Cygnus | 19 Jan 2026
Friend-shoring is reshaping lithium, rare earth and graphite supply chains, creating a resilience premium and new winners and losers in clean tech.

The New Oil (Part 4): Can Technology Break the Dependency?
By Cygnus | 16 Jan 2026
Can magnet recycling and rare-earth-free motors reduce global dependence on strategic minerals? Part 4 explores breakthroughs, limits and timelines.









